Find website vulnerabilities using Uniscan vulnerability scanner
Uniscan is a simple Remote File Include, Local File Include, and Remote Command Execution vulnerability scanner. It can scan for directories, files, robot.xml, web fingerprint and server fingerprint. The programming language used to develop Uniscan tool is Perl. You can extend the tool and it supports plugins.
Kali Linux and Parrot operating system include Uniscan Tool in their distribution. You don't have to install it in those operating systems.
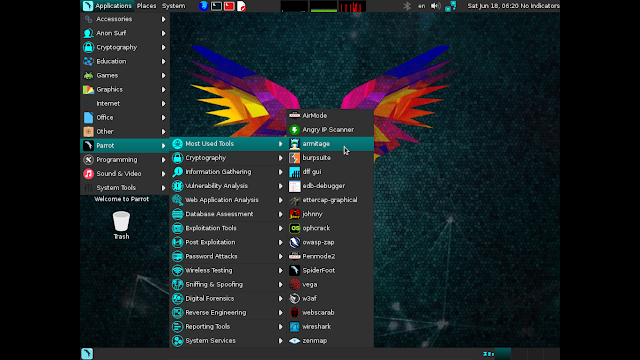
There are two ways to launch the application. You can use the command line version or GUI version. The GUI version is located in Web Application Analysis then Web Crawlers & Directory Bruteforce menu (Parrot OS). You need to provide administrative access to run the Uniscan.
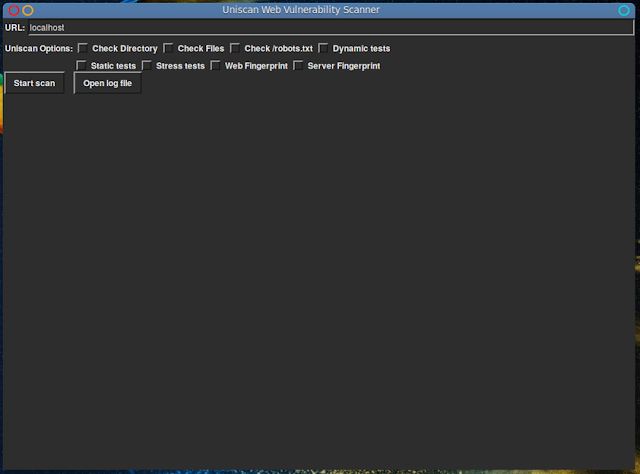
To start the scan enter the web address and select all options that you would like to scan. Then click the scan button. It will take a couple of minutes to scan for vulnerabilities. You can check the log file by clicking the "Open log file" button.
Alternatively, you can launch the Uniscan tool using the Terminal. If you use Terminal to launch the Uniscan tool, make sure you have already provided the administrative access. You can do this by entering the "su" command. Enter the "uniscan" to launch the tool.
Enter the following command to scan a URL for directory checks, file checks, robot.txt check, sitemap.xml file check, dynamic and static check. You can start help file using "uniscan -h". Following example use multiple options. Some tools and applications require you to separate options with space. However, you can state all those options without space like the following command.
uniscan -u https://silvertrinity.com -qweds
The Uniscan tool generates HTML report after the scan. It is stored in the "/usr/share/uniscan/report" folder.
If you use the File Explorer, you will see images folder and CSS file. If you copy the report another location, you have copy those folders and files as well.
If the Uniscan tool doesn't pick any vulnerabilities the server may be protected using technology such as reverse proxy (Cloudflare provides reverse proxy service) to blocks all the scanner spiders that scan the website.
Kali Linux and Parrot operating system include Uniscan Tool in their distribution. You don't have to install it in those operating systems.
There are two ways to launch the application. You can use the command line version or GUI version. The GUI version is located in Web Application Analysis then Web Crawlers & Directory Bruteforce menu (Parrot OS). You need to provide administrative access to run the Uniscan.
To start the scan enter the web address and select all options that you would like to scan. Then click the scan button. It will take a couple of minutes to scan for vulnerabilities. You can check the log file by clicking the "Open log file" button.
Alternatively, you can launch the Uniscan tool using the Terminal. If you use Terminal to launch the Uniscan tool, make sure you have already provided the administrative access. You can do this by entering the "su" command. Enter the "uniscan" to launch the tool.
Enter the following command to scan a URL for directory checks, file checks, robot.txt check, sitemap.xml file check, dynamic and static check. You can start help file using "uniscan -h". Following example use multiple options. Some tools and applications require you to separate options with space. However, you can state all those options without space like the following command.
uniscan -u https://silvertrinity.com -qweds
The Uniscan tool generates HTML report after the scan. It is stored in the "/usr/share/uniscan/report" folder.
If you use the File Explorer, you will see images folder and CSS file. If you copy the report another location, you have copy those folders and files as well.
If the Uniscan tool doesn't pick any vulnerabilities the server may be protected using technology such as reverse proxy (Cloudflare provides reverse proxy service) to blocks all the scanner spiders that scan the website.



Comments
Post a Comment