Gather sub domains from a domain using Sublist3r for penetration testing
Sublist3r is a python tool designed to enumerate subdomains of websites using OSINT. It helps penetration testers and bug hunters collect and gather subdomains for the domain they are targeting. Sublist3r enumerates subdomains using many search engines such as Google, Yahoo, Bing, Baidu, and Ask. Sublist3r also enumerates subdomains using Netcraft, Virustotal, ThreatCrowd, DNSdumpster, and ReverseDNS.
subbrute was integrated with Sublist3r to increase the possibility of finding more subdomains using brute-force with an improved word list. The credit goes to TheRook who is the author of subbrute.
You can install Sublist3r by cloning the Sublist3r repository. However, you can use the package manager to install it in Debian based operating systems.
Open the Terminal and enter the following commands.
apt update && apt -y install sublist3r
To list all the basic options use -h option. It shows all the functionalities that supported by the Sublist3r.
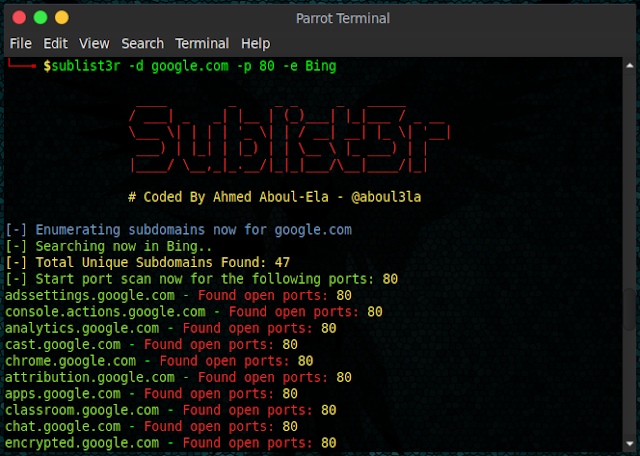
Following command search for subdomains in the google.com domain. Option -d is used to specify the domain address. Option -p is used to specify the port number. You can search for multiple ports such as 80 and 443 (Separate ports by comma). You can specify the search engine using option -e.
sublist3r -d google.com -p 80 -e Bing
subbrute was integrated with Sublist3r to increase the possibility of finding more subdomains using brute-force with an improved word list. The credit goes to TheRook who is the author of subbrute.
You can install Sublist3r by cloning the Sublist3r repository. However, you can use the package manager to install it in Debian based operating systems.
Open the Terminal and enter the following commands.
apt update && apt -y install sublist3r
To list all the basic options use -h option. It shows all the functionalities that supported by the Sublist3r.
Following command search for subdomains in the google.com domain. Option -d is used to specify the domain address. Option -p is used to specify the port number. You can search for multiple ports such as 80 and 443 (Separate ports by comma). You can specify the search engine using option -e.
sublist3r -d google.com -p 80 -e Bing



Comments
Post a Comment